Introduction:
The first products using these chips are hitting the streets this Fall and more are expected over the next year. This new technology could have broad implications for content producers; possible uses include music and video delivery, games, applications, books, reference materials, and databases.
Rob Enderlee, an industry analyst from the Enderlee Group who has been covering technology since the early 90s, thinks 3DM will change content delivery via portable devices. "They are the missing link," he says. "We have had read-only media for music, games, and certain types of applications for a very long time, but haven't had read-only, non-volatile memory for much of anything. I would argue that there has been a segment of this market waiting for a low-cost way to deliver software to multiple portable devices." Enderlee also points out that this is a much lower cost medium than typical flash media.
In the past, the high cost of memory kept this type of delivery system out of reach of many publishers. Steer says, "The economics didn't work out for a lot of publishers to afford to put their content on a chip and sell their content at reasonable price points. [By] bringing the price point down for solid state memory, it now becomes a medium that is affordable for publishers to use."
This could have an especially big effect in the digital music and video markets by providing a low-cost delivery system for video and music content on portable players. "One example is that there are certain types of players coming out later this year—portable media players—something that fits in your pocket with a backlit color screen that takes memory cards or cartridges and plays full video or music," says Steere. Mattel released one such player in October they have dubbed the "Juicebox," a handheld video and music player that uses pre-recorded cartridges based on Matrix 3-D Memory as the means to store and play content.
Enderlee predicts other possible uses such as using blank 3DM chips in portable devices to record video and music from content kiosks in malls, train stations, or airports. "Consumers could go to a kiosk, select songs, and have them delivered on a read-only medium, with DRM maintained, to an iPod or RealPlayer without the likelihood that they could share them broadly with friends or neighbors, something that content providers have wanted to [eliminate]," he says.
Another possible use for 3DM is as digital film. Unlike conventional digital camera flash memory, which you can write to many times, consumers could purchase a 3DM chip and use it in the same way they use film cameras by taking the pictures, then taking the chip to a shop to make prints. Enderlee sees this as an attractive model to some consumers who are used to the film paradigm. "You have a large number of people who want to do it the way they have always done it. This would allow them to use the digital camera very much like a film camera," according to Enderlee.Enderlee believes the initial 3DM chips will come with content on them and that the blank chip market (with the exception of the digital film scenario) will take off as capacities increase. "Utility increases as capacity increases," he says.
The first products using these chips are hitting the streets this Fall and more are expected over the next year. This new technology could have broad implications for content producers; possible uses include music and video delivery, games, applications, books, reference materials, and databases.
Rob Enderlee, an industry analyst from the Enderlee Group who has been covering technology since the early 90s, thinks 3DM will change content delivery via portable devices. "They are the missing link," he says. "We have had read-only media for music, games, and certain types of applications for a very long time, but haven't had read-only, non-volatile memory for much of anything. I would argue that there has been a segment of this market waiting for a low-cost way to deliver software to multiple portable devices." Enderlee also points out that this is a much lower cost medium than typical flash media.
In the past, the high cost of memory kept this type of delivery system out of reach of many publishers. Steer says, "The economics didn't work out for a lot of publishers to afford to put their content on a chip and sell their content at reasonable price points. [By] bringing the price point down for solid state memory, it now becomes a medium that is affordable for publishers to use."
This could have an especially big effect in the digital music and video markets by providing a low-cost delivery system for video and music content on portable players. "One example is that there are certain types of players coming out later this year—portable media players—something that fits in your pocket with a backlit color screen that takes memory cards or cartridges and plays full video or music," says Steere. Mattel released one such player in October they have dubbed the "Juicebox," a handheld video and music player that uses pre-recorded cartridges based on Matrix 3-D Memory as the means to store and play content.
Enderlee predicts other possible uses such as using blank 3DM chips in portable devices to record video and music from content kiosks in malls, train stations, or airports. "Consumers could go to a kiosk, select songs, and have them delivered on a read-only medium, with DRM maintained, to an iPod or RealPlayer without the likelihood that they could share them broadly with friends or neighbors, something that content providers have wanted to [eliminate]," he says.
Another possible use for 3DM is as digital film. Unlike conventional digital camera flash memory, which you can write to many times, consumers could purchase a 3DM chip and use it in the same way they use film cameras by taking the pictures, then taking the chip to a shop to make prints. Enderlee sees this as an attractive model to some consumers who are used to the film paradigm. "You have a large number of people who want to do it the way they have always done it. This would allow them to use the digital camera very much like a film camera," according to Enderlee.Enderlee believes the initial 3DM chips will come with content on them and that the blank chip market (with the exception of the digital film scenario) will take off as capacities increase. "Utility increases as capacity increases," he says.
Advanced Technology Seminar 1
XQuery processing is one of the prime research topics of the database community, as is evident from the number of systems and publications. Systems, architectures, principles, and algorithms rapidly emerge for all its incarnations; be it in message/file transformations, XML caching, XML content management, or XML-based publishing and mediator systems.
At the same time, XQuery research is still in a "pre-paradigmatic" stage, where the conventional symptoms of the stage are observed: It is hard to piece together point efforts into a big picture. Similarities and interplay opportunities between parallel efforts are "lost in the translation" across the different paradigms. This is a natural stage in the evolution of most science and technology topics and our references to the classic 1930's works of Kuhn on the development and evolution of science will make sure the audience gets rid of any guiltiness we may accidentally create. Nevertheless, the time is ready for the next stage: The goal of this tutorial is to "federate" among the plethora of works, and categorize existing work and future topics along a few reference paradigms that fuse existing works around a reference architecture.
The focus will be on database-oriented issues, in the sense of focusing on issues and drawing parallels with the principles and techniques of database systems, as follows: We will provide a quick overview of relevant standards as abstractions, such as: XQuery/XPath data model and its labeled tree counterpart, a classification of XQuery usages, and an outline of an XQuery processing reference architecture. Then, we will delve into the details of logical-level XQuery optimization, discussing tree-pattern style abstractions, sub-expression factorization, and view-based query answering. We will then turn to physical level optimization, briefly discussing storage, indexing and relational shredding schemes for XML.
 Ioana ManolescuIoana Manolescu is a researcher in the Gemo group in INRIA Futurs, France. Ioana has obtained her PhD in 2001 from University of Versailles and INRIA, France, working on query optimization for distributed databases, and XML. Her thesis work on distributed query optimization was incorporated into the Medience French start-up. She has worked as a post-doc in Politecnico di Milano, Italy, extending the WebML web modelling model to cope with Web services and workflow specification. Her current research topics include XML data storage, query algebras and query processing, XML compression, XML data cleaning, and distributed data and process management based on Web services. Ioana has (co-)authored several tutorials and advanced courses for the EDBT database summer school. More information on Ioana's projects can be found at http://www-rocq.inria.fr/~manolesc.
Ioana ManolescuIoana Manolescu is a researcher in the Gemo group in INRIA Futurs, France. Ioana has obtained her PhD in 2001 from University of Versailles and INRIA, France, working on query optimization for distributed databases, and XML. Her thesis work on distributed query optimization was incorporated into the Medience French start-up. She has worked as a post-doc in Politecnico di Milano, Italy, extending the WebML web modelling model to cope with Web services and workflow specification. Her current research topics include XML data storage, query algebras and query processing, XML compression, XML data cleaning, and distributed data and process management based on Web services. Ioana has (co-)authored several tutorials and advanced courses for the EDBT database summer school. More information on Ioana's projects can be found at http://www-rocq.inria.fr/~manolesc. Yannis PapakonstantinouYannis Papakonstantinou is an Associate Professor of Computer Science and Engineering at the University of California, San Diego. His research is in the intersection of database and Internet technologies. Yannis has published over fifty research articles in scientific conferences and journals, given tutorials at major conferences, and served on journal editorial boards and program committees for numerous international conferences and symposiums. He was the co-Chair of WebDB 2002, the co-Chair of XIME-P 2004, the General Chair of ACM SIGMOD 2003 and the Vice PC Chair for the "XML, Metadata and Semistructured Data" track of IEEE ICDE 2004. In 1998, Yannis received the NSF CAREER award for his work on integrating heterogeneous data. In 2000 Yannis founded Enosys Software, which built the first generally available distributed XQuery processor, along with software for XML-based integration of distributed sources, and was sold in 2003 to BEA Systems. Yannis holds a Diploma of Electrical Engineering from the National Technical University of Athens and MS and Ph.D. in Computer Science from Stanford University (1997). His complete bio is available at http://www.db.ucsd.edu/people/yannis.htm
Yannis PapakonstantinouYannis Papakonstantinou is an Associate Professor of Computer Science and Engineering at the University of California, San Diego. His research is in the intersection of database and Internet technologies. Yannis has published over fifty research articles in scientific conferences and journals, given tutorials at major conferences, and served on journal editorial boards and program committees for numerous international conferences and symposiums. He was the co-Chair of WebDB 2002, the co-Chair of XIME-P 2004, the General Chair of ACM SIGMOD 2003 and the Vice PC Chair for the "XML, Metadata and Semistructured Data" track of IEEE ICDE 2004. In 1998, Yannis received the NSF CAREER award for his work on integrating heterogeneous data. In 2000 Yannis founded Enosys Software, which built the first generally available distributed XQuery processor, along with software for XML-based integration of distributed sources, and was sold in 2003 to BEA Systems. Yannis holds a Diploma of Electrical Engineering from the National Technical University of Athens and MS and Ph.D. in Computer Science from Stanford University (1997). His complete bio is available at http://www.db.ucsd.edu/people/yannis.htm Advanced Technology Seminar 2
Efficient execution of ranking query is increasingly becoming a major challenge for database technology. Nowadays, many applications have requirements that can only be matched by a combination of information retrieval systems and DBMSs. DBMSs provide efficient update, indexing, concurrency and recovery. On the other hand, IR on text and multimedia requires techniques involving uncertainty and ranking for effective retrieval. A true integration is likely to require significant changes in the standard database techniques for indexing and query optimization and may require new query languages.
The main goal of this seminar is to give an in-depth look on supporting ranking queries as an increasingly interesting area of research. We cover the state-of-the-art techniques in research prototypes and industry-strength database engines for efficient handling of ranking and top-k queries. We give an inclusive background on ranking, voting and rank-aggregation algorithms. Then we give a detailed coverage of ranking query models--covering top-k selection and top-k join queries, and the various approaches recently proposed by researchers to support these queries in database systems. We focus primarily on how to integrate ranking as a new query processing and optimization dimension, with the aim of supporting ranking queries as a basic and core functionality. The seminar identifies several challenges that need to be addressed towards a true support for ranking and effective retrieval in database management systems.
This seminar is targeted at general database researchers. The seminar is also of interest to audience with industrial background as it describes and summarizes different attempts to integrate new functionalities in industrial database management systems. The seminar gives several motivating examples and challenging applications that are in real need for efficient handling of ranking queries. More importantly, the seminar highlights some interesting challenges in rank-aware query processing and optimization.
Ihab F. IlyasIhab F. Ilyas is an assistant professor at the school of computer Science, University of Waterloo. He obtained his Ph.D. in 2004 from Purdue University, and an M.Sc. and a B.Sc. from the University of Alexandria, Egypt. His main research interests include advanced query processing and optimization, self-managing and adaptive computing, and non-traditional database systems (e.g., multimedia and spatial databases). In his recent Ph.D. thesis, he has introduced novel query processing and optimization techniques for top-k queries in relational database systems. For more information, visit http://db.uwaterloo.ca/~ilyas
Walid G. ArefWalid G. Aref is an associate professor of computer science at Purdue University. His research interests are in developing database technologies for emerging applications, e.g., spatial, multimedia, genomics, and sensor databases. He is also interested in indexing, data mining, and geographic information systems (GIS). His research has been supported by the NSF, Purdue Research Foundation, CERIAS, Panasonic, and Microsoft Corp. In 2001, he received the CAREER Award from the National Science Foundation. He is in the editorial board of the VLDB Journal and is a member of the ACM and the IEEE. For more information, visit http://www.cs.purdue.edu/~aref
Tiny chips flash memory advance
Flash memory chips are used in MP3 players and digital camerasElectronics giant Samsung has shown off what it claims is the world's most powerful chip for use in memory cards.
The 64 gigabit (Gb) chips could be used to make 128 gigabyte memory cards, commonly used in MP3 players, capable of holding the equivalent of 80 DVDs.
The chips are built using circuits with a minimum feature size of just 30 billionths of a metre (nanometre).
Rival firm Toshiba has said it is also working with similar technol
 ogy. Both firms will release products in 2009.
ogy. Both firms will release products in 2009.Flash advance
Flash memory is a so-called non-volatile computer memory, primarily used in memory cards, USB drives and MP3 players.
Non-volatile memory retains information even when there is no power to the device.
Samsung said there was currently "exploding demand" for flash memory as a storage medium in a range of applications.
The new chips are designed to be used in a specific type of memory known as NAND flash.
NAND is one of two types of flash memory and offers higher storage and faster speeds than the cheaper NOR flash.
NOR is commonly used in low-end applications where smaller memory capacity and slower speeds are acceptable, such as in cheaper mobile phone handsets.
Samsung has said that a single chip could be used in an MP3 player capable of holding 18,000 songs.
Combining 16 chips would allow 128GB devices, the company said, making Flash a rival to hard drives.
"This has the biggest storage capacity of a single memory chip ever developed in the world," Kwon Hyosun of the firm told AFP.
Toshiba announced its plans to use 30nm technology earlier this month.
"Our goal is to gain an edge over rivals by supplying the most advanced chips before anyone else," a spokeswoman for Toshiba said at the time.
The proliferation of digital video and audio content has created a big problem for the owners of this content. How do you protect your intellectual property from illegal transfer to non-authorized users of music, movies, and other valuable entertainment and infotainment property? The problem is making video and audio products easily accessible to authorized users who have paid for the right to listen to or view these products and non-accessible to those who have not.
Secure protection systems are necessary components of digital content protection and encryption keys are critical components of these systems. The security of such keys must be paramount--if a key is stolen, the entire system is compromised, valuable content may be lost, and the owner of this content may lose huge amounts of money.
The solution lies in emerging protocols and interfaces that permit the transfer of encrypted high-quality video and audio streams that can be decrypted and used only by authorized “receivers.” Currently, the HDCP Authentication protocol and HDMI interfaces are gaining wide acceptance for the secure passing of video and audio streams. Also needed are the supporting technologies that support HDCP-compliant and HDMI-enabled equipment, including non-volatile memory (NVM) storage of the device keys and identifiers this type of equipment requires.
The market for devices receiving audio and video content is quite large and continuing to grow very rapidly. In 2005, research firm iSuppli predicted shipments of MP3 players to rise by nearly a factor of four from 2004 to 2009. The firm stated that total MP3 player shipments would expand to 132 million units in 2009, rising at a Compound Annual Growth Rate (CAGR) of 29.1% from 36.8 million units in 2004. In January of 2006, research firm InStat reported that digital cable set-top box worldwide unit shipments reached 12.2 million in 2005, up from 10.8 mi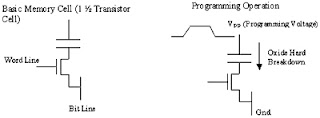 llion in 2004. Also in January 2006, the Digital Entertainment Group, an industry trade organization, said an estimated 37 million DVD players were sold to U.S. consumers in 2005, with nearly 17 million DVD players sold in the fourth quarter alone. Growth should continue strong with the introduction of and acceptance of the two next-generation blue laser DVD formats, Blu-ray and HD-DVD. Finally, along with these “dedicated” digital content receiver devices, one should not forget the cell phone – in mid-2005, Gartner Dataquest estimated that almost 800 million units would be sold during the year, a 16% increase over 2004.
llion in 2004. Also in January 2006, the Digital Entertainment Group, an industry trade organization, said an estimated 37 million DVD players were sold to U.S. consumers in 2005, with nearly 17 million DVD players sold in the fourth quarter alone. Growth should continue strong with the introduction of and acceptance of the two next-generation blue laser DVD formats, Blu-ray and HD-DVD. Finally, along with these “dedicated” digital content receiver devices, one should not forget the cell phone – in mid-2005, Gartner Dataquest estimated that almost 800 million units would be sold during the year, a 16% increase over 2004.
HDCPIntel developed HDCP (High-bandwidth Digital Content Protection) in 2001 as a Digital Rights Management (DRM) system to protect digital audio and video content traveling across Digital Visual Interface (DVI) or High Definition Multimedia Interface (HDMI) connections. The FCC approved HDCP as a "Digital Output Protection Technology" in August of 2004. With the HDCP protocol, a video receiver, some type of display, confirms to a video transmitter that the receiver is authorized to receive the protected content by demonstrating knowledge of a set of secret device keys. Each authorized device is provided with a unique set of secret device keys from the Digital Content Protection (DCP) LLC, which licenses HDCP to manufacturers. The communication exchange, which lets the receiver demonstrate knowledge of these keys, also lets the receiver and transmitter generate a shared secret value to demonstrate receiver authorization, one that cannot be intercepted during this exchange. Thus the shared secret can be used as a symmetric key to encrypt video content intended only for the authorized receiver.
Each authorized receiver receives an array of 40, 56-bit secret Device Keys and a corresponding identifier from DCP. This identifier, a 40-bit word containing exactly 20 ones and 20 zeros, is the Key Selection Vector (KSV) assigned to the receiver. Each bit in the KSV corresponds to one of the forty Device Keys, and every compliant device is required to permanently store both keys and KSV in a secure internal location. Each HDCP-compatible transmitter and receiver has a KSV all to itself, which allows for the transmitter and receiver to communicate their encryption to each another in order to ensure the validity of their content protection. Only after a two-part encryption process occurs will the transmitter begin to send information to the receiver.
HDMIHDMI, like DVI, permits uncompressed video transfer between a digital-video source and HDMI-enabled video receiver, normally a consumer electronics device such as a digital television. One difference between the two is that HDMI transfers both video and audio signals while DVI only carries a video signal. Encryption is done by an HDMI transmitter found in the video source, such as a DVD player or set-top box, while decryption is done by the HDMI receiver, such as an HDTV display. HDMI supports standard, enhanced, or high-definition video, plus multi-channel digital audio on a single cable. It transmits all ATSC HDTV standards and supports 8-channel digital audio, with extra bandwidth available for future enhancements and requirements.
For HDMI-enabled equipment, a video display device, upon obtaining an HDCP license from DCP, will have to securely store the 40, 56-bit secret device keys and 40-bit Key Selection Vector--this requires an in-the-field programmability capability.
HDMI-enabled equipment operating under the HDCP protocol goes through three major steps during a content transfer. First, the source (transmitter) and receiver go through an authentication procedure to verify that a receiver is licensed to receive protected content. Authentication starts with the transmitter sending its KSV as a public key along with a pseudo-random number to a receiver. The receiver also sends its public KSV to the transmitter. If the receiver's KSV is valid, the transmitter and receiver each use their own Device Keys and the other device's KSV to generate the Content Key. Each device adds together those of its device keys that correspond to the twenty bits set to 1 in the other device's KSV. If both sets of Device Keys and KSVs are valid, the two Content Keys will be identical and are used as symmetric keys to encrypt and decrypt the content stream from the transmitter. To further ensure the integrity of the system, the actual Content Keys are never passed through the connection.
In addition, the devices must also make sure that the receiver is not on a revocation list for having keys and a KSV stolen from an authorized receiver. As part of the HDCP licensing agreement, each receiver must store a list of revoked keys that are included with all new HDPC-licensed devices and distributed with media such as DVDs used in HDCP devices. Only then, if the host is “safe,” is the data is sent encrypted, to prevent eavesdropping of the protected content, and then decrypted by the receiver.
Key Storage OptionsThe need for in-the-field programming eliminates ROM as a memory option. Flash memory would, at first, appear to be a good choice for NVM storage, but it also has problems. Embedded flash, with additional masks and processing steps, adds significant cost to an HDMI transmitter or receiver chip. The security of flash is also suspect, since the state of the individual memory bits can be read with voltage contrast or other scanning techniques, thus revealing Device Keys and KSV.
Embedded fuses represent another technology that can be used to store security keys and IDs is embedded fuse links – either metal or polysilicon. However, fuse trimming must be done at the wafer level – packaged chips cannot be laser trimmed. This precludes the use of laser trimming for applications such as HDCP key storage, since the Device Keys and KSV are not available to a receiver until after chip fabrication and may also be updated in the field if the keys are compromised.
The NVM technology used to store this type of information should reside on the HDMI receiver and transmitter chips, for both security and cost considerations. Since most video display devices are in the consumer market segment, the addition of the NVM to store the Device Keys and KSV should add little, if any, additional cost to the receiver; ideally, no extra cost. This indicates a technology that can be implemented on a standard CMOS logic chip with no additional masks or processing steps. Finally, the NVM memory technology should be scalable to new process nodes, allowing HDMI-enabled chip manufacturers to take advantage of the lower cost and enhanced feature-set capability of chips manufactured with new silicon processes.
Non-Volatile Memory for HDMI/HDCP DevicesFloating-gate technologies such as flash have security, data retention and scalability problems. Another, newer memory IP technology, Extra Permanent Memory (XPM), does not depend on injection and charge tunneling to and from a floating gate to store ones and zeros. Instead, the one-time programmable (OTP) XPM memory cell uses a very short channel MOS transistor which looks like a capacitor (an open circuit) in the unprogrammed state. When programmed by a short high-voltage pulse, the gate oxide suffers a permanent breakdown and the transistor conducts like a resistor (a closed circuit) with low impedance (a few tens of Kohms). However, the memory cell does not add any additional leakage current during normal operation, keeping power consumption low (Figure 1).
Figure 1. The XPM cell uses a short programming voltage pulse to break down the oxide in a short-channel transistor, thus converting an open circuit into a closed one.
Secure protection systems are necessary components of digital content protection and encryption keys are critical components of these systems. The security of such keys must be paramount--if a key is stolen, the entire system is compromised, valuable content may be lost, and the owner of this content may lose huge amounts of money.
The solution lies in emerging protocols and interfaces that permit the transfer of encrypted high-quality video and audio streams that can be decrypted and used only by authorized “receivers.” Currently, the HDCP Authentication protocol and HDMI interfaces are gaining wide acceptance for the secure passing of video and audio streams. Also needed are the supporting technologies that support HDCP-compliant and HDMI-enabled equipment, including non-volatile memory (NVM) storage of the device keys and identifiers this type of equipment requires.
The market for devices receiving audio and video content is quite large and continuing to grow very rapidly. In 2005, research firm iSuppli predicted shipments of MP3 players to rise by nearly a factor of four from 2004 to 2009. The firm stated that total MP3 player shipments would expand to 132 million units in 2009, rising at a Compound Annual Growth Rate (CAGR) of 29.1% from 36.8 million units in 2004. In January of 2006, research firm InStat reported that digital cable set-top box worldwide unit shipments reached 12.2 million in 2005, up from 10.8 mi
 llion in 2004. Also in January 2006, the Digital Entertainment Group, an industry trade organization, said an estimated 37 million DVD players were sold to U.S. consumers in 2005, with nearly 17 million DVD players sold in the fourth quarter alone. Growth should continue strong with the introduction of and acceptance of the two next-generation blue laser DVD formats, Blu-ray and HD-DVD. Finally, along with these “dedicated” digital content receiver devices, one should not forget the cell phone – in mid-2005, Gartner Dataquest estimated that almost 800 million units would be sold during the year, a 16% increase over 2004.
llion in 2004. Also in January 2006, the Digital Entertainment Group, an industry trade organization, said an estimated 37 million DVD players were sold to U.S. consumers in 2005, with nearly 17 million DVD players sold in the fourth quarter alone. Growth should continue strong with the introduction of and acceptance of the two next-generation blue laser DVD formats, Blu-ray and HD-DVD. Finally, along with these “dedicated” digital content receiver devices, one should not forget the cell phone – in mid-2005, Gartner Dataquest estimated that almost 800 million units would be sold during the year, a 16% increase over 2004.HDCPIntel developed HDCP (High-bandwidth Digital Content Protection) in 2001 as a Digital Rights Management (DRM) system to protect digital audio and video content traveling across Digital Visual Interface (DVI) or High Definition Multimedia Interface (HDMI) connections. The FCC approved HDCP as a "Digital Output Protection Technology" in August of 2004. With the HDCP protocol, a video receiver, some type of display, confirms to a video transmitter that the receiver is authorized to receive the protected content by demonstrating knowledge of a set of secret device keys. Each authorized device is provided with a unique set of secret device keys from the Digital Content Protection (DCP) LLC, which licenses HDCP to manufacturers. The communication exchange, which lets the receiver demonstrate knowledge of these keys, also lets the receiver and transmitter generate a shared secret value to demonstrate receiver authorization, one that cannot be intercepted during this exchange. Thus the shared secret can be used as a symmetric key to encrypt video content intended only for the authorized receiver.
Each authorized receiver receives an array of 40, 56-bit secret Device Keys and a corresponding identifier from DCP. This identifier, a 40-bit word containing exactly 20 ones and 20 zeros, is the Key Selection Vector (KSV) assigned to the receiver. Each bit in the KSV corresponds to one of the forty Device Keys, and every compliant device is required to permanently store both keys and KSV in a secure internal location. Each HDCP-compatible transmitter and receiver has a KSV all to itself, which allows for the transmitter and receiver to communicate their encryption to each another in order to ensure the validity of their content protection. Only after a two-part encryption process occurs will the transmitter begin to send information to the receiver.
HDMIHDMI, like DVI, permits uncompressed video transfer between a digital-video source and HDMI-enabled video receiver, normally a consumer electronics device such as a digital television. One difference between the two is that HDMI transfers both video and audio signals while DVI only carries a video signal. Encryption is done by an HDMI transmitter found in the video source, such as a DVD player or set-top box, while decryption is done by the HDMI receiver, such as an HDTV display. HDMI supports standard, enhanced, or high-definition video, plus multi-channel digital audio on a single cable. It transmits all ATSC HDTV standards and supports 8-channel digital audio, with extra bandwidth available for future enhancements and requirements.
For HDMI-enabled equipment, a video display device, upon obtaining an HDCP license from DCP, will have to securely store the 40, 56-bit secret device keys and 40-bit Key Selection Vector--this requires an in-the-field programmability capability.
HDMI-enabled equipment operating under the HDCP protocol goes through three major steps during a content transfer. First, the source (transmitter) and receiver go through an authentication procedure to verify that a receiver is licensed to receive protected content. Authentication starts with the transmitter sending its KSV as a public key along with a pseudo-random number to a receiver. The receiver also sends its public KSV to the transmitter. If the receiver's KSV is valid, the transmitter and receiver each use their own Device Keys and the other device's KSV to generate the Content Key. Each device adds together those of its device keys that correspond to the twenty bits set to 1 in the other device's KSV. If both sets of Device Keys and KSVs are valid, the two Content Keys will be identical and are used as symmetric keys to encrypt and decrypt the content stream from the transmitter. To further ensure the integrity of the system, the actual Content Keys are never passed through the connection.
In addition, the devices must also make sure that the receiver is not on a revocation list for having keys and a KSV stolen from an authorized receiver. As part of the HDCP licensing agreement, each receiver must store a list of revoked keys that are included with all new HDPC-licensed devices and distributed with media such as DVDs used in HDCP devices. Only then, if the host is “safe,” is the data is sent encrypted, to prevent eavesdropping of the protected content, and then decrypted by the receiver.
Key Storage OptionsThe need for in-the-field programming eliminates ROM as a memory option. Flash memory would, at first, appear to be a good choice for NVM storage, but it also has problems. Embedded flash, with additional masks and processing steps, adds significant cost to an HDMI transmitter or receiver chip. The security of flash is also suspect, since the state of the individual memory bits can be read with voltage contrast or other scanning techniques, thus revealing Device Keys and KSV.
Embedded fuses represent another technology that can be used to store security keys and IDs is embedded fuse links – either metal or polysilicon. However, fuse trimming must be done at the wafer level – packaged chips cannot be laser trimmed. This precludes the use of laser trimming for applications such as HDCP key storage, since the Device Keys and KSV are not available to a receiver until after chip fabrication and may also be updated in the field if the keys are compromised.
The NVM technology used to store this type of information should reside on the HDMI receiver and transmitter chips, for both security and cost considerations. Since most video display devices are in the consumer market segment, the addition of the NVM to store the Device Keys and KSV should add little, if any, additional cost to the receiver; ideally, no extra cost. This indicates a technology that can be implemented on a standard CMOS logic chip with no additional masks or processing steps. Finally, the NVM memory technology should be scalable to new process nodes, allowing HDMI-enabled chip manufacturers to take advantage of the lower cost and enhanced feature-set capability of chips manufactured with new silicon processes.
Non-Volatile Memory for HDMI/HDCP DevicesFloating-gate technologies such as flash have security, data retention and scalability problems. Another, newer memory IP technology, Extra Permanent Memory (XPM), does not depend on injection and charge tunneling to and from a floating gate to store ones and zeros. Instead, the one-time programmable (OTP) XPM memory cell uses a very short channel MOS transistor which looks like a capacitor (an open circuit) in the unprogrammed state. When programmed by a short high-voltage pulse, the gate oxide suffers a permanent breakdown and the transistor conducts like a resistor (a closed circuit) with low impedance (a few tens of Kohms). However, the memory cell does not add any additional leakage current during normal operation, keeping power consumption low (Figure 1).
Figure 1. The XPM cell uses a short programming voltage pulse to break down the oxide in a short-channel transistor, thus converting an open circuit into a closed one.
SUMMARY OF THE INVENTION
The present invention provides for a non-volatile semiconductor memory device to be connected to a serial ATA (SATA) cable which is an interface supportive of high data transfer speeds.
In one embodiment, a serial advanced technology attachment (SATA) storage device for connecting to an SATA cable includes at least one non-volatile semiconductor memory for storing data therein; an SATA adapter, connected to the SATA cable, for transferring/receiving data signals to/from the SATA cable; a memory controller for controlling the non-volatile semiconductor memory in response to the data signals transferred from the SATA adapter; and an SATA device controller, connected between the SATA adapter and the memory controller, for interfacing transmitted/received signals between the SATA adapter and the memory controller.
The SATA connector and the SATA device controller may include a serial physical interface plant block for converting electrical signals received via the SATA cable into logical signals; a serial digital transport link block for receiving the logic signals from the serial physical interface plant block to process the logical signals to generate data suitable for SATA protocol communication; and a serial digital transport control block, connected between the serial digital transport link block and the memory controller, for interfacing the data transmission/reception between the serial digital transport link block and the memory controller.
The serial digital transport control block includes a shadow register block for generating control values which are necessary for the transfer of write/read data to/from the non-volatile semiconductor memory.
The memory controller includes a reader for reading the control values stored in the shadow register block; a command detector for detecting a command from the control values read out by the reader; a setter for setting a special function register in response to the command detected by the command detector in order to correspond to the control values stored in the shadow register block a memory interface block for controlling data writing/reading/erasing operations in the non-volatile semiconductor memory based upon the set content in the special function register; and a data handler, connected between the shadow register block and the memory interface block, for managing data to be written in the non-volatile semiconductor memory or data read out from the non-volatile semiconductor memory.
The present invention provides for a non-volatile semiconductor memory device to be connected to a serial ATA (SATA) cable which is an interface supportive of high data transfer speeds.
In one embodiment, a serial advanced technology attachment (SATA) storage device for connecting to an SATA cable includes at least one non-volatile semiconductor memory for storing data therein; an SATA adapter, connected to the SATA cable, for transferring/receiving data signals to/from the SATA cable; a memory controller for controlling the non-volatile semiconductor memory in response to the data signals transferred from the SATA adapter; and an SATA device controller, connected between the SATA adapter and the memory controller, for interfacing transmitted/received signals between the SATA adapter and the memory controller.
The SATA connector and the SATA device controller may include a serial physical interface plant block for converting electrical signals received via the SATA cable into logical signals; a serial digital transport link block for receiving the logic signals from the serial physical interface plant block to process the logical signals to generate data suitable for SATA protocol communication; and a serial digital transport control block, connected between the serial digital transport link block and the memory controller, for interfacing the data transmission/reception between the serial digital transport link block and the memory controller.
The serial digital transport control block includes a shadow register block for generating control values which are necessary for the transfer of write/read data to/from the non-volatile semiconductor memory.
The memory controller includes a reader for reading the control values stored in the shadow register block; a command detector for detecting a command from the control values read out by the reader; a setter for setting a special function register in response to the command detected by the command detector in order to correspond to the control values stored in the shadow register block a memory interface block for controlling data writing/reading/erasing operations in the non-volatile semiconductor memory based upon the set content in the special function register; and a data handler, connected between the shadow register block and the memory interface block, for managing data to be written in the non-volatile semiconductor memory or data read out from the non-volatile semiconductor memory.